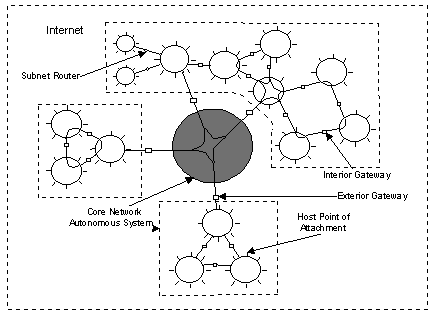
Figure 1: General Internet architecture [10]
28.11.1999
Pradip Lamsal
Department of Computer Science and Engineering
Helsinki University of Technology
Pradip.Lamsal@hut.fi
Abstract
Security of the Internet has become a critical issue especially when more and more financially sensitive corporations are starting to use the Internet to conduct their business . All kinds of information have to be secured before they are sent through the Internet. Routing information is very important to the routers as it updates the routing tables. These routing tables later determine where other messages should be routed. Failure to send correct routing information can result in other messages being routed to wrong destination and this can create security problems in the network.
The core network, which uses BGP routing protocol, has several security threats. Different techniques have been used in the past at the application layer to make the transaction secure. Now, some countermeasures are implemented in lower layers such as transport layer and network layer but they still do not guarantee secure transactions. This paper looks at major threats to BGP routing information and discusses the countermeasures that can be applied at different layers to secure BGP routing information.
Contents
2 Network Architecture & BGP
2.1 Internet architecture
2.1.1 Autonomous system
2.1.2 Core network
2.2 Routing protocols
2.2.1 IGP
2.2.2 EGP
2.3 BGP
3 BGP Security Threats
3.1 What is network security?
3.2 Security available in BGP
3.3 Intruders
3.4 Threats to routing information
3.4.1 BGP threats
4 Countermeasures
4.1 Application layer
countermeasures
4.1.1 Encryption
4.1.2 Authentication
4.1.3 Message sequence number
4.1.4 Timestamp
4.1.5 Access control
4.2 Transport layer countermeasures
4.3 Network layer countermeasures
4.3.1 How
IPSec can be used to protect BGP packets?
4.4 Miscellaneous
4.4.1 Intrusion detection
4.4.2 Security management tools
4.4.3 Firewalls
The use of the Internet has grown exponentially in the last few years, both in corporate and private sectors. More and more businesses are conducted on the Internet and people have become more dependent on the networking technology than ever before. At the same time, the Internet has displayed a variety of vulnerabilities existing in underlying networks, Internet protocols, network administration and host systems [12]. Several vulnerabilities have been detected in security mechanisms of hosts, networks and routing technologies. This presents big threats both to business oriented Internet users and to normal Internet users. These threats can range from simple email attacks to highjacking of financially sensitive information such as credit card numbers.
Over the last few years people have become more sensitive about the security issues on the Internet. Different security mechanisms have been introduced to tackle different problems. Security measures at the application layer have been available for some time. These security measures can be customized for different applications. Transport layer can also implement its own security mechanisms and they are independent of the application. Similarly, standards on securing data at the network layer are also coming out and these security measures can be applied to any IP packets, independent of the application and the transport layer protocol.
This paper mainly focuses on the security aspects of BGP,
a routing protocol used in the core network. Section 2 briefly introduces
the Internet architecture and BGP. Section 3 identifies threats to BGP
messages, section 4 discusses the countermeasures to those threats, section
5 analyzes security mechanisms at different layers and finally section
6 draws some conclusions on how those security mechanisms can be used to
secure BGP messsages.
The Internet is a collection of different autonomous systems connected together by the core network as shown in Figure 1.

Figure 1: General Internet architecture [10]
An autonomous system (AS) is a collection of networks and subnetworks. One AS is independent of another AS, it has its own routing algorithm and it can be managed independently. One network is connected to another network by a gateway called the interior gateway. The protocol an interior gateway uses to route a packet inside an autonomous system is called the Interior Gateway Protocol (IGP). The IGP used in an autonomous system can be different than that in another autonomous system. In telecommunications domain an autonomous system is often called an access network.
The autonomous systems are connected together in a form of a network called the core network or the backbone network. The gateways that connect all the autonomous systems to the core network are called exterior gateways and the routing protocol these exterior gateways use is called the Exterior Gateway Protocol (EGP). Unlike IGPs the EGP cannot be different on different exterior gateways and it must be an internetwide standard.
One of the most widely used IGPs is Routing Information Protocol (RIP). This protocol uses a technique called Distance Vector Algorithm (DVA), which is specific to TCP/IP. Link State (LS) and Open Shortest Path First (OSPF) are other examples of commonly available interior gateway protocols.
Border Gateway Protocol (BGP) is an EGP used in TCP/IP networks. Current BGP, BGP4, is capable of carrying routing information only for IPv4. Some extensions have been added to this protocol so that it can be used for other network layer protocols such as IPv6. And, this new protocol is called BGP4+.
BGP is a distance-vector routing protocol, which means that a router calls only its neighbors to send all or some part of its routing table. The main function of a BGP speaking system is to exchange network reachability information with other BGP systems. This reachability information includes information on the list of ASs, which this reachability information goes through. BGP runs over a reliable transport protocol such as TCP. [2]
The only two things that have been added to BGP4 so that it supports IPv6 are:
In simple terms, network security means securing the network from intruders, i.e., protecting the confidential information from those who do not need to access it and protect the network resources from malicious users [5]. It means protecting the information and the resources from both the people outside the network and the people inside the network.
The BGP protocol itself is not very promising in terms of security. The contents of a BGP packet is just another type of data for the underlying transport and network layer protocols. BGP4+, which is aimed for IPv6, does not change any security issues of BGP4. So, the protocol itself does not promise much to overcome security problems.
An intruder is an entity capable of attacking the network. Intruders can modify, replay, monitor, fabricate or delete any of the network traffic. In a network, which runs BGP, there can be several types of intruders as listed below:
Section 3.1 mentions that network security involves securing the data and the network resources. When considering threats to a network these two areas can be viewed separately, however, most of the threats relate to both of them. Protecting the integrity of a network is critical in protecting the information it contains [5]. When considering what to protect in a network, one is concerned with maintaining the integrity of the physical network, network software and any other network resources [5].
When threats to BGP packets are considered they cannot be seperated from other threats related to IP packets as a whole. This section discusses the threats directly related to BGP packets and categorizes these threats into two broad categories.
The threats in a core network involve threats to the routing traffic and threats to the data traffic. Here, only threats to the routing traffic are considered.
3.4.1.1 Deception or disruption of routing messages
Deception or disruption of a routing message involves modifying, replaying, fabricating and even deleting the routing message. This kind of attack generally results in modifying the routing structure of a BGP host or the whole network which can cause denial of services, disclosoure of network traffic and inaccurate accounting of network resource usage.
The vulnerabilities these attacks exploit are the
lack of access control, authentication and integrity of the BGP messages.
[15]
3.4.1.2 Disclosure of routing messages
It is not very difficult for an intruder to get access to routing messages. From this routing messages one can easily get the next hop to reach a destination and path taken by traffic to different destinations. The next hop information might not be confidential all the time. However, the path taken to reach different destinations can be confidential in some circumstances. The attacks to obtain this path information include:
Since the BGP packets ultimately travel through the network as IP packets it is very essential to understand the security mechanisms included in all the layers: application, transport and network. These three layers can have different and independent security mechanisms and BGP can take full advantage of all the lower layers' security mechanisms.
The next subsections discuss the security countermeasures at application, transport and network layers.
4.1 Application layer countermeasures
Application layer countermeasures refer to those security mechanisms, which can be applied to BGP packets before they are sent down to the transport layer. By applying these mechanisms the packets can be "secured" no matter what kind of transport and network layer are used.
Every single message going between the peer routers can be encrypted for security. This can be done by first exchanging a session key between the routers after the connection has been established and then using this key to encrypt all the messages for that given session. Encryption provides authenticity and integrity of the messages travelling between two routers. If any corruption is detected then the link can be terminated.
Authentication refers to verifying the host or the person who it claims to be. There are several mechanisms to authenticate a user or a host but the most common one is the use of passwords. Authentication can be made more secure by the use of digital signatures.
Each of the routing messages can be digitally signed by the sender. There are several algorithms available including the RSA algorithm for his purpose. Digital signature provides authentication and some kind of integrity. This mechanism protects from message modification but not from replay. However, it can be used in conjunction with other mechanisms such as message sequence number and timestamps (explained in the next subsection) to disable replay attack.
Each BGP message can have a message sequence number attached to it. At the start this number for a given link is initialized to zero and incremented by one. This mechanism helps find any skipped or replayed message. If this happens the connection can be terminated using the NOTIFICATION message. One thing that is important to note here is the size of the sequence number. Normally the size is made big so that the number does not go back to zero. In case this happens the connection is terminated and a new connection is established with a new session key. [3] [15]
Timestamps are used to prevent a router updating its routing table by some old and out of date information. Timestamp generally involves attaching the time-of-creation information to the message itself. The way in which this is implemented depends on the type of possible attack. Three common timestamping methods are summarized below.
4.1.4.1 Timestamp with hash cache
In this mechanism the sender sends the message with a timestamp. When the receiver receives the message it checks the messageís timestamp with its local time and finds out whether this message is within the time window of the given source or not. This time window is known to the receiver in advanced. If the message is not within the acceptable window, then the message is rejected straight away. If the message is accepted then a hash is computed using a previously defined key. This hash is then compared with the list of hashes corresponding to the given source (this list is stored in the cache). If the hash is in the cache then the receiver knows that the message is a replayed message and thus it rejects this new message. If it is not in the cache then it is an acceptable message and is accepted. After the message has been accepted the receiver stores this hash in its cache for future comparison.
In this mechanism the timestamp of the received message is first checked using the window mechanism described in the previous section. If the message is within the acceptable window then the timestamp is further checked with the timestamp of the last accepted message. The timestamp of the accepted message is saved by the receiver all the time. If this new timestamp is greater than the timestamp of the last accepted message then the receiver knows that the new message is not old and thus accepts this message. After this new message has been accepted the timestamp corresponding to this message is saved for future comparison.
In the time window mechanism clock synchronization is very important. The senderís clock can drift forward or backward. If this happens the message with a timestamp can fall outside the receiverís window and validation of the message can fail. In order to prevent this kind of failure the clocks are adjusted appropriately.
High-level access control is normally implemented by strong authentication mechanisms. The countermeasures described above such as encryption, timestamps and digital signature can be used to control the access of an entity to the network resources.
4.2 Transport layer countermeasures
There have been new implementations of security mechanisms at the transport layer. This new implementations are based on Transport Layer Security (TLS) Protocol, previously famous as SSL (Secure Sockets Layer) Protocol. SSL was developed and published by Netscape. TLS is independent of the application and therefore can be used for any kind of packets including BGP routing information packets. At the moment this protocol is mostly used with HTTP. [1] [18]
TLS consists of two main components: TLS record protocol and TLS handshake protocol. TSL record protocol provides privacy and data integrity. It encrypts data using symmetric cryptography to provide privacy and keyed message authentication digest to provide data integrity. TLS handshake protocol is responsible for authenticating server and client to each other and for negotiating the encryption algorithm to be used by the TLS record protocol. [1] [18]
4.3 Network layer countermeasures
The network layer countermeasures do not depend on the transport or application layer and they apply to any kind of application. IPSec, a protocol suite designed to provide privacy and authentication services at the IP layer, is becoming popular among the research scientists as this protocol suite has recently become a standard. [8] This section summarizes how IPSec can be used to secure BGP packets.
4.3.1 How IPSec can be used to protect BGP packets?
The main feature of this protocol suite is that it provides security services at the network layer. It lets the system select the required security protocols, define the algorithms and put in place any cryptographic keys required to provide the requested services. The main services IPSec provides are access control, data integrity (even connectionless), authentication, rejection of replayed packets, data confidentiality (encryption) and a bit of traffic flow confidentiality.
Since the IP packets encapsulate the upper layer protocols these services are automatically available to any upper layer protocols given that the IPSec protocol suite is used in IP. What this means is that the upper layer protocols such as TCP, UDP, ICMP and BGP are automatically protected by IPSec. And these services do not have to be necessarily implemented in those layers. [8] [14]
AH (Authentication Header) and ESP (Encapsulation Security Payload) are the two major protocols used in IPSec to provide traffic security. Details of those protocols can be found in [6] and [7] respectively. They can be summarized as follows:
Intrusion detectors can detect known attacks and alert administrators. They can be either network based or host based. In a network based system each packet entering the network is examined to detect any pattern that matches the known attack methods. In a host-based system the detection mechanism is run on the background on each individual host within the monitored network and it detects probes of host ports, password guessing and other known attack methods.
4.4.2 Security management tools
Several security management tools can be used to secure the system. Such tools include network vulnerability tool that can gather information about the network and analyze potential security problems, security scanner that can scan a host or a network to test for a common set of security flaws and error in configuration, password-guessing tool, and promiscuous-mode IP sniffer.
A firewall is a system that acts as a barrier between
two network segments. A firewall can be a packet filter or an application
gateway. A packet filter firewall screens all the packets before forwarding
them to another host whereas an application gateway filters application
level data streams instead of IP packets. [11]
This section outlines some major advantages and disadvantage
of the application layer security mechanisms and network layer security
mechanisms. [4] Transport layer security mechanisms
are not not analyzed here.
| Advantage | Disadvantage | |
| Application layer security mechanisms |
|
|
| Network layer security mechanisms |
|
|
Like any other application, BGP cannot control the TCP/IP infrastructure and hence cannot influence the security measures taken at the transport and the network layers. The security mechanisms implemented in the lower layers improves the security of the network as a whole. However, considering fact that the lower layer security is still not effective BGP routing information should not only rely on the lower layer security measures but should also include some of its own application layer countermeasures.
Data integrity is probably the most critical issue in
BGP routing information. Incorrect routing information not only updates
the routing table of the core routers incorrectly but also routes the packets
to the wrong network. Therefore, strong measures must be taken at the application
layer to maintain data integrity. New protocols proposed for transport
layer and network security guarantee privacy. For the BGP speakers it is
very important that the data is authenticated properly. Digital signatures
can be used between the BGP speakers. Since one BGP speaker talks to its
neighbour routers only, it is possible to use some kind of key based authentication
mechanism. Besides authentication, the right timing of the routing information
is equally important for the BGP routers. Hence, out of date routing messages
must be rejected. Message sequence numbers and timestamps can be very useful
to avoid replay attack and out of date routing message.
[1] Apostolopoulos, G., Peris, V. & Saha, D., Transport Layer Security: How much does it really cost?, IEEE, 1999
[2] Bates, T., Chandra,
R., Katz, D. & Rekhter, Y., A Border Gateway Protocol 4 (BGP-4), RFC
1771, 1996
http://www.cis.ohio-state.edu/htbin/rfc/rfc1771.html
[3] Bates, T., Chandra,
R., Katz, D. & Rekhter, Y., Multiprotocol Extensions for BGP-4, RFC
2283, 1998
http://www.cis.ohio-state.edu/htbin/rfc/rfc2283.html
[4] Caronni, G., Lubich, H., Aziz, A., Markson, T. & Skrenta, R., SKIP Securing the Internet, IEEE, 1996
[5] Cisco, Cisco
Security Technologies, 1999
http://www.cisco.com/univercd/cc/td/doc/cisintwk/ito_doc/security.htm
[6] Kent, S. &
Atkinson, R., IP Authentication Header, RFC 2402, 1998
http://www.cis.ohio-state.edu/htbin/rfc/rfc2402.html
[7] Kent, S. &
Atkinson, R., IP Encapsulating Security Payload (ESP), RFC 2406, 1998
http://www.cis.ohio-state.edu/htbin/rfc/rfc2406.html
[8] Kent, S. &
Atkinson, R., Security Architecture for the Internet Protocol, RFC 2401,
1998
http://www.cis.ohio-state.edu/htbin/rfc/rfc2401.html
[9] Murphy, S., L. & Badger, M., R., Digital Signature Protection of the OSPF Routing Protocol, IEEE, 1996
[10] Lamsal, P.,
Management of Next Generation IP Core Network, HUT 1999
http://www.tcm.hut.fi/Opinnot/Tik-110.551/1999/papers/12ManagementOfIPngCore/ipcore.html
[11] Landwehr, C & Goldschlag, D, Security Issues in Networks with Internet Access, IEEE, 1997
[12] Lichtenstein, S., Developing Internet Security Policy for Organizations, IEEE, 1997
[13] Oppliger R., Security at the Internet Layer, IEEE, 1998
[14] Sirois, K. E & Kent, S. T., Securing the Nimrod Routing Architecture, IEEE, 1997
[15] Smith, B. R & Garcia-Luna-Aceves, J. J, Securing the Border Gateway Routing Protocol, IEEE, 1996
[16] Smith, B., R., Murthy, S. & Garcia-Luna-Aceves, J., J., Securing Distance-Vector Routing Protocols, IEEE, 1997
[17] Thayer, R.,
Doraswamy, N. & Glenn, R., IP Security Document Roadmap, RFC 2411,
1998
http://www.cis.ohio-state.edu/htbin/rfc/rfc2411.html
[18] Dierks, T & Allen, C.,
The TSL Protocol,Version 1.0, RFC 2246, 1999
http://www.cis.ohio-state.edu/htbin/rfc/rfc2246.html
Cisco, Routing basics, 1999
http://www.cisco.com/univercd/cc/td/doc/cisintwk/ito_doc/routing.htm