Figure: "LANMAN hash" algorithm
Petteri Laamanen
Department of Computer Science
Helsinki University of Technology
Firewalls are too often the first and only line of defense for corporate computer networks. If administrators want their networks to be safe also the other components should support the desired security level. Servers are very important components in this task. This paper tries to illustrate the current security situation of NT Server operating system. Current situation is illustrated with the help of several examples. In conclusions suggestions are made for administrators to make their networks safer and for Microsoft to enhance the NT Server security. The suitability of NT Server for different kinds of environments in the light of these examples is also evaluated.
1 Introduction
2 Sources of security flaws
2.1 Bad configurations
2.2 Bad software engineering
2.2.1 Passwords are
encrypted with weak cryptographic algorithms
2.2.2 Internet
Explorer Exploit #4
2.2.3 Network
Monitor, remote commands and CIFS
2.3 Bugs and bad implementation
2.3.1 Winnuke
2.3.2 Ping o' Death
2.3.3 GetAdmin
2.3.4 RedButton
2.4 Trojan horses and viruses
2.4.1 Phony
PKZip archive is in fact a Trojan horse program
2.4.2 A potential password change exploit
2.4.3 Macro Trojan
horses
2.4.4 Master
Boot Record viruses and Boot Record viruses
2.4.5 DOS
and Windows viruses
2.4.6 Macro
viruses and NT viruses
3 Sources for further information
3.1 Crackers' and Hackers'
Web pages
3.2 Security
companies, security Web sites and security organizations
3.3 Microsoft
3.4 Books
3.5 Tools
4 Future
5 Conclusions and suggestions
6 Glossary
7 References
Firewalls are often the first and much too often the only line of defense of corporate computer networks. A firewall can control traffic between the enterprise's internal network and external network such as Internet. Many companies think that they have reduced the network security risk enough when they have installed the firewall. Unfortunately this is a wrong illusion. According to Fortune Magazine 30 percent of all break-ins involving the Internet took place despite the presence of a firewall. [1] FBI statistics show that more than 60 percent of computer crimes originate from within the enterprise. [2]
In an NT environment a firewall can be used for example to disable access to UDP and TCP ports 137,138 and 139. NT servers use these ports for NBT (NetBios over TCP/IP) services. The NBT protocol is used for administering the servers as well as for sharing resources such as hard disks, printers and databases. Once these ports cannot be reached from the external network the NetBios interface is much harder to exploit. [3] Today's firewalls can be seen as a logical equivalent to the World War II Maginot line. The line was practically impenetrable. However an attack around the line through neighboring countries completely circumvented the line. The analogy implies to corporate networks as well. Firewalls must be present but at the same time also the servers should be made secure against resourceful attackers. Servers and their operating systems should be ready to defend against both malicious crackers from outside that have passed the firewall and the attackers from inside. [2]
The security of corporate computer network is a term that has both a business meaning and a technical meaning. Security depends on proper administration of systems, client and server, as well as observation of related business procedures, physical access control and audit functions. [4] This document shall concentrate primarily on the technical aspects.
Today's corporate networks are built from many different computer and operating systems. Operating systems are working together and many times open links from a system to another do exist. Thus a break-in into one system may give access to another systems also. Two small security defects in different systems that look very harmless alone can lead into great security threat when put together in a certain environment. [5] This paper focuses on the NT Server operating system alone. This paper does not consider NT connections to other systems such as NetWare or Samba UNIX servers.
This paper tries to illustrate a snapshot of the current situation of NT server security issues. Issues are presented with the help of several examples. Presented examples will not cover exhaustively the whole wide spectrum of threats but tries to concentrate on the hottest issues present at the moment. The Internet Explorer Exploit #4 is taken into this paper for two reasons. The Internet Explorer browser comes with the default installation of the operating system and administrators may very well use it to access information in Internet during administrative tasks. The second reason is that it illustrates well the kinds of problems that LAN originated operating system meet when they are used in Internet.
The core of NT Server operating system is a modern and secure. NT operating system has a C2 classification when floppy drive is removed, no network components are installed and registry and file systems security settings are configured properly. [3] Unfortunately the C2 accredited configuration is quite not useful for most of the users.
Microsoft has been quite fast in fixing the simple security flaws such as the Winnuke bug for example. [6] Unfortunately the situation is sometimes not so good with the more fundamental design and implementation flaws. In these cases Microsoft has been either denying the relevance of the flaws or pointing at flaws in other operating systems. Examples of Microsoft using these kinds of approaches can be read from an EE Times article about a dinner between Microsoft managers from Redmond and members of L0pth society at <URL:http://techweb.cmp.com/eet/whitepaper/paper1/paper1a.html>. [7]
Microsoft fixes the security flaws with two kinds of packages: hot fixes and service packs. Hot fixes are small packages that fix one or only few security issues or bugs in the operating system. Sometimes one may have to pay for Microsoft to do these customizations. Service Packs are much bigger packages and they usually include all the hot fix patches and other bug fixes as well as new features to the operating system itself. Service packs are publicly available and free of charge. [3]
Because new security holes are found and the old ones are patched all the time the security status is under continuous change. In the following chapters some of the bigger security issues that exist today are represented with examples. Naturally there are many more security issues present at the moment and more to come in the future.
The default configuration of NT Server 3.51 right after installation is insecure. Many things are configured almost as if computer was designed for personal use. In general system settings and registry settings are too loose. File permissions allow practically everybody to do almost everything by default. Registry settings are in much better shape by default. There are lists of recommendable registry and file system setting changes both in the literature and in the Web. For example books such as Windows NT Security: A Practical Guide to Securing Windows NT Servers and Workstations by Charles B. Rutstein [8] and Windows NT Security Guide by Stephen A. Sutton [9] both have pragmatic security check lists. Documents like Windows NT Security Issues: Practical recommendations for securing File System and Registry at NTSecurity.com [10] or Coopers & Lybrand L.L.P.'s white paper on Microsoft Windows NT Server: Security Features and future directions [11] are both accessible through Internet and include good checklists for making NT Server more secure. The down side of these lists is that none of them is exhaustive. Administrators who want to keep their system as secure as possible will have to go through all the different lists and keep on eye on all the different mailing lists and newsgroups. On top of all this some of the settings differ between the lists and sometimes contradiction occur. Administrators have to find out them selves what settings are the best for them. This takes a lot of time. Especially in the smaller companies where the administration is done on top of other duties, the operating system is left in its original state. "What I don't know won't hurt me" is too many times the principle in use. [2]
As examples of bad default security configurations right after installation, the following could be named. The default administration account is always called Administrator and the password can be left blank. There is no limit on unsuccessful logon attempts and thus there is no lock out period after unsuccessful logon attempts. Barely no auditing is enabled by default and it is up to the administrator to decide what to audit and how to audit. Everybody has access to almost all the directories in NT server. Remote registry access might be granted to other users than administrators.[11]
Even if you get the system configured securely in the beginning some of the default settings suggested by the computer are such that security threats appear if caution is not used during the later configuration changes. For example when sharing a directory in the network the operating system suggests all rights to All Users by default on share level. All Users does not mean all authenticated and authorized users but all the users that can access the computer via network or keyboard. Administrators have to be careful to remember to change these settings every time they share a directory. This is not a lot of work but can be easily forgotten as the sharing happens quite infrequently.
Things have become somewhat better with the release of NT Server 4.0. The default configuration of NT is a little bit more secure and there are new ways of preventing the exploitation through the network. For example there is a new registry entry that disables the network access to registry from others than administrators. By default the new registry entry enables remote registry editing only for NT server administrators. Still NT Workstation's new registry entry is configured by default to allow anybody to access the registry remotely as long as they have sufficient rights inside the registry. [11]
Problems associated with bad software engineering are probably the most difficult to solve. Some of the reasons for bad software engineering come from the strict US export regulations for strong cryptographic systems. Others come from backward compatibility and new operating system add-ons in general.
Encryption method
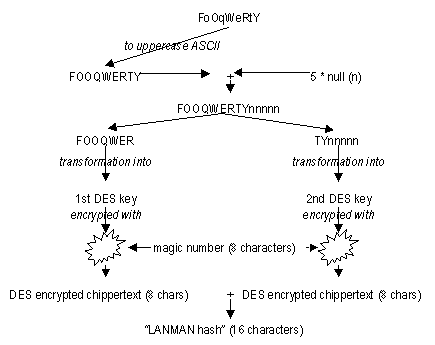
Maybe one of the most severe problems is the weak encryption of NT passwords. NT Server 3.51 saves the passwords in registry in two formats both in "LANMAN hash" and MD4 hash. LANMAN hash in used for backward compatibility to old LAN MANAGER and Windows clients. LANMAN hash is infamous for its' weakness and can be very easily cracked with brute force techniques. Next, the process of producing a LANMAN hash is described in detail to illustrate how weak the old hash is.
LANMAN hash is made from the user's password by converting characters to uppercase ASCII and then catenating so many nulls in the end of the string that the total length of the password string is 14 characters. Then the password string is divided into two separate strings of 7 characters. These two new 7 character long strings are used as DES keys. Both of these two DES keys are used for encrypting an 8 character magic number. The result is two different cipher text strings. These two cipher text strings are catenated and the result is the "LANMAN hash". LANMAN hash is one way algorithm and cannot be reversed. But since the used encryption keys are 7 characters long and there are only 26 characters (A-Z) to choose from even the brute force attack is still feasible. In a brute force attack a password generator goes through systematically all the different password candidates at a time. The LANMAN hash is generated and the hash is compared with the original hash. [12]

Figure: "LANMAN hash" algorithm
Strength of the password hashes
I tested the feasibility of brute force attack with Pentium 120 MHz machine that had 48 MB of memory. The program I used was l0pht's l0phtCrack version 1.5. The test file contained LANMAN hashes and MD4 hashes of six individual users. Two of the users had a password straight out of dictionary. These passwords were cracked in 3 seconds. Three users had the same password and username. These passwords were cracked in 2 minutes. One of the user accounts had a proper password with uppercase letters, lowercase letters and numbers. Even the worst case estimate for cracking this password was well under 60 hours. This test demonstrates well that cracking the NT's password is really no problem when both LANMAN hashes and MD4 hashes are available.
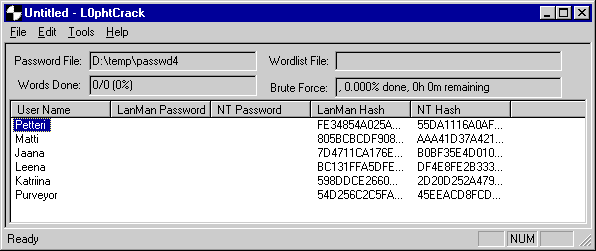
Screen capture: The GUI of L0pthCrack 1.5
The MD4 hash is much stronger since the password string is not chopped into two halves and uppercase and lowercase letters are interpreted as different characters. The only problem is that once the LANMAN hash is broken the MD4 password can be easily tested by trying through all the different combinations of uppercase and lowercase letter strings for the known password.[12]
Different methods of getting the password hashes
But how do we get the password hashes? Microsoft NT Server passwords can easily be captured in two ways. They can be taken straight from the registry where they are hidden or they can be captured from the network for example with a protocol analyzer. In the registry, password hashes are stored in the SAM part of the registry. Everybody who has a read permission to these parts of the registry can obtain the password hashes. If a user does not know how to get the password hashes he can always use programs such as PWDUMP.EXE to dump the usernames and password hashes into an ASCII file. And if the user does not have enough rights, he can usually get administrative rights by running a program such as GetAdmin on the console.[13] The other way to capture password hashes is to record challenge response pairs in network. Challenge response pairs hold the information needed for authentication and a part of this information are the password hashes. Usually the packets contain both LANMAN hashes and MD4 hashes. If file system resources are accessed over Internet challenge response pairs can be captured in all of the nodes on the route. If the traffic is between computers inside the company a simple "protocol analyzer" such as Microsoft Network Monitor is needed for capturing the packets.[12]
Two separate hot fixes were made to patch these security holes: Key fix and a LM-fix. Both of the fixes are written only for NT Server 4.0. Both of these security fixes are just workarounds for the problem that is brought to NT with backward compatibility to older systems such as LAN MANAGER. They won't make the password hashes themselves any stronger.
Key fix
Microsoft released a Key fix against the registry break-ins. After the Key fix hostile users can still extract the passwords from the registry but will not be able to crack them with conventional cracking programs. Key fix encrypts the original password hashes in registry with a 128 bit Password Encryption Key. This Password Encryption key is stored in the registry and it is itself encrypted with another key called System Key or Boot Key. Thus the confidentiality of the password hashes is primarily dependable on where and how the System Key is stored. There are three alternate locations for the System key to be stored in. It can be stored in the registry with complex absfucation, or it can be generated from the password given during the boot process, or it can be loaded from a floppy. The fist solution is terrible because once you find out how the System Key is stored you will be able to extract it from every system you meet. The latter two options are quite suitable as long as the password given during the boot up is selected carefully. [12]
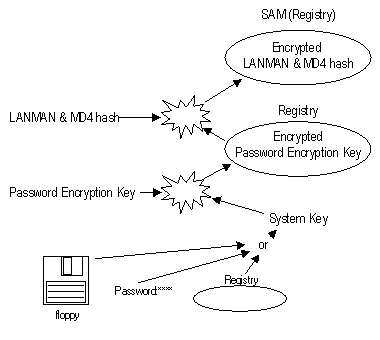
Figure: Password hash encryption after Key fix
LM-fix
The LM-fix removed the LANMAN hash from the challenge-response pairs. This way even if the challenge-response pair could be recorded the only information that a recorder would get are the MD4 password hashes. MD4 hashes are cryptographically much stronger. When it takes the maximum of 60 hours to break a LANMAN hash with a brute force method it takes 2200 years to break a MD4 hash in the worst case. [12] Even though the MD4 is stronger than LANMAN hashes it is know to have flaws and is not recommended to use when strong algorithms are needed. There are probably better ways than brute force algorithm to crack a MD4 hash. Individual substeps of the cracking procedure have been demonstrated but nobody has come up with a complete algorithm yet.[10]
If grabbing the password hashes from registry or recording them with a protocol analyzer does not scare you the Internet Explorer Exploit #4 should. Internet Explorer Exploit #4 is also known with the name of HTML Variant Exploit. With the help of this exploit a malicious cracker doesn't even have to try to break in the target network to get the passwords, but can lay back and collect the usernames and passwords from his own server. For example the cracker can use a free sex picture archive as a disguise and collect the usernames and passwords as a main business.
Web pages are usually authored with HTML and delivered to client browsers with HTTP protocol. Images on the web page such as pictures in GIF format are not included in the main document but only their download location is described in the document. The images are downloaded separately to the browser and rendered to the web page as soon as they are downloaded. Usually the image's download location is referred to with a relative embedded tag like the one below.
<img src="\images\friendly.gif"">.
Tags can also include absolute paths such as
<img src="file:/\\10.0.0.1\hacks\trouble.gif">.
In the latter case Internet Explorer thinks that user wants to download the image from a file server and starts an SMB session. (SMB protocol is used for example for authentication in Windows environment.) Internet Explorer sends the Domain name, the Username and the Password to IP-address 10.0.0.1 with no notice to user. If the server at IP address 10.0.0.1 is a hostile one it can record the packets and crack the password hashes. This design was originally made because file servers and their network drives were wanted to be seen as just one kind of web resource. This was a good idea but unfortunately the cryptographic strength of the old password hashes is not enough for Internet use.
What makes this design even worse is the possibility of clients and servers to negotiate the authentication scheme. Windows clients cannot lie and they use always the safest possible challenge-response pairs. Unfortunately some other clients (from sources other than Microsoft) are able to lie during the authentication scheme negotiation and may force the other party to use plain text authentication even if it is not needed. In this case your password goes unencrypted through the Internet. If you have Microsoft's Internet Explorer installed in your computer you can test the feature. This feature can be tested for example at <URL:http://www.securenetworks.net/>. Remember to change your password before and after the test! [12]
There is no easy way to patch this painful security flaw. The efficient use of proxy servers and firewalls to filter out the SMB traffic between the internal and external networks is the only way. For example all the browsers may be forced to use a proxy server. After this the proxy server and the firewall filter out all the SMB traffic going outside the corporate network. The solution is too complex and requires too much protocol expertise and time for a normal administrator to handle. In most cases the security flaw will remain. [12]
The use of Network Monitor can be locked behind a password. This password should never be the same as administrator's password. Passwords should never be the same because Network Monitor's password is extremely easy to crack. [11]
Remote commands such as rcopy, rexec should be installed only after careful consideration because their security level is very low. Fortunately these command do not come with the default installation of NT. These commands come with Resource Kit. [11]
Microsoft's new Internet file system CIFS is developed from the old SMB protocol. For this reason it has inherited some of the SMB's severe security holes. Hobbit explains these flaws in great detail in his paper "CIFS Common Insecurities Fail Scrutiny". CIFS is intended to be used in Internet but much of its' design is still from its' old LAN origin [15].
Most of the denial of service attacks in NT server environment are based on bugs and bad implementation. What is also interesting is that many of the newer attack methods are published with a program that can be used for launching the attack. For example Winnuke and Red Button attacks were both published with a program that is easy to use and has a graphical user interface. The attacker doesn't need to know anything about the attack method itself. The IP address of the target machine is enough to launch the attack.
Winnuke program has a graphical user interface with entry fields for IP address and nuke message, and a launch button. After user has given this information he pushes the button and the attack is complete. The remote computer will crash. Winnuke does this by contacting port 139 in the foreign host and sending some Out of Bound data. If the remote computer has Windows NT, Windows 95 or Windows 3.x without latest service packs the target machine's TCP/IP stack will go down. Usually it causes also a General Protection Fault. A blue screen appears and the computer has to be restarted.
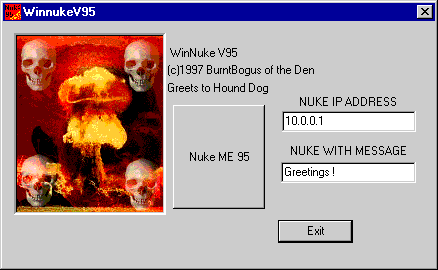
Screen capture: The GUI of Winnuke program
Winnuke incident shows that Microsoft is interested in fixing some of the bugs quite fast. Winnuke program was published May 7th, 1997. The writer of the program was an anonymous person who called him/herself _eci. Five days later on May 12th, 1997 Microsoft released patches for Windows NT 3.51 and 4.0. These patches didn't work in all the environments because the TCP/IP stack of the MacOS uses a little bit different implementation for setting the "Urgent Pointer". Ten days from last patch on May 22nd, 1997 Microsoft released new patches that permanently cured the OOB and Urgent Pointer bugs. The links to final patches can be found for example at <URL:http://206.148.240.160/~dirk/winnuke.html> under the section patches and they can also be downloaded from <URL:http://www.microsoft.com/security>. [12]
Another denial of service attack is the Ping o' Death. It is by no means an NT only attack method. There are 18 major operating systems (e.g. all Windows, Linux, Solaris, NEXTSTEP, SCO Unix etc. ) and devices such as routers, network printers etc. that can be brought onto their knees with this attack. Basically every system that has a TCP/IP stack may be vulnerable to this attack method. The attack is based on fragmented IP datagrams and on the fact that most of the systems cannot handle fragmented IP datagrams correctly if they are too long.
According to RFC's the IP packets can be up to 65 535 (2^16 - 1) octets long. An ICMP ECHO packet is typically built from 20 octets of IP header information plus 8 octets of ICMP ECHO header. Hence the maximum size of data in an ICMP ECHO packet is 65 535 - 20 - 8 = 65 507 octets. The source of this exploit comes from the way that fragmented IP packets are put together after they are received from the network. When an IP packet is sent to transport media it is chopped to smaller fragments if it cannot be fitted inside a single transport layer packet. Each of these fragments include an offset value that tells the fragments position inside the IP packet. In the receiving end the protocol stack gets fragments of the IP packet from the transport layer. It puts together the fragments and passes the packet to next layer as soon as all the fragments have arrived and the IP packet is complete. In the last fragment it is possible to have (offset + size of the packet) > 65 535. Usually machines do not process the fragments until all the fragments of the packet are present. If the size of the each fragment is not verified and the total size of the packet is over 65 535 bytes, it is possible to get an internal 16 bit variable to overflow. This overflow usually leads to system crashes, reboots and kernel dumps.
This exploit is not tied to the ping program or the ICMP ECHO protocol alone. Every application and protocol that sends IP datagrams is vulnerable to this attack. Since the IP datagrams are the basic building block of the net and almost every protocol uses them, including TCP, UDP, NFS, telnet, http and so on. Patches against this exploit are included in the latest NT Service Packs. [16]
The GetAdmin program uses an NT 4.0 bug to gain administrative rights on a local computer. To get the administrative privileges, the user needs to log on locally (by keyboard) to a computer he wants to attack. Then he runs the GetAdmin utility, which gives him administrative privileges to that computer. After this he can do everything that a legitimate administrator could do. He might dump the password hashes and crack the passwords at home or he could make a new administrative user account for later use.
Microsoft has introduced a hotfix against this problem and it can be downloaded from <URL:http://www.microsoft.com/security/issues.htm>. There are rumors going around in the newsgroups that Microsoft's patch corrects only those bugs used by the GetAdmin program but that there are several other this kind of bugs that can be exploited for the same purpose. One should be aware of these rumors but must not react too strongly because they are only rumors. [13]
NT security model usually requires a valid username and password for user authentication but in certain cases user can also log on anonymously without presenting username or password. This anonymous user is authorized as the default Guest account if the Guest account is enabled. Guest account brings security risks and should always be disabled. (Microsoft Knowledgebase article ID: Q101232) [17] RedButton bug gains unauthorized access to the server resources even without the Guest account through utilizing the predefined Everyone group. The flaw gives read and write access to all the sensitive information in file system and registry that is available to Everyone group. It also gives the name of the built-in Administrator account to demonstrate how little impact can be gained with renaming the account.
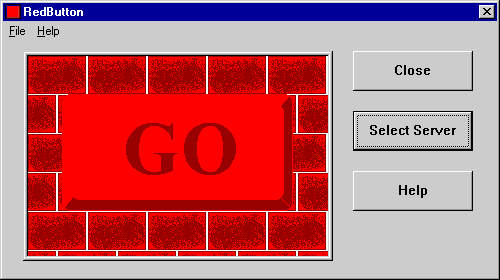
Screen capture: The GUI of RedButton program
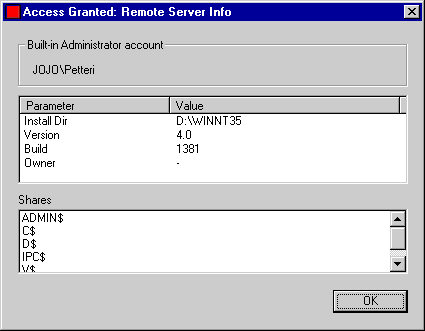
Screen capture: The information that RedButton program collected from the server during
the attack
There is also a program called RedButton that uses this RedButton bug. The program has a graphical user interface and is extremely easy to use. Anybody can use it. The writers of the program have not wanted to do any harm. This is why the program only reads the sensitive information from the registry. This bug could certainly be used for malicious purposes just by rewriting the program to change the values in registry.[18]
Administrator can go around the RedButton bug by disabling the predefined Guest account and taking all the permissions away from default Everyone group. If an account is needed for representing all the users, a new group named for example AllUsers should be created and the permissions should be given explicitly to this new group. The suggested solution will not eliminate all the problems but will be a practical cure in most of the cases. Replacing Everyone group in all the Registry entries and file system ACLs is a huge task but can be made much easier with the help of utility programs. Examples of these programs are mentioned in the chapter 3 Sources for further information. [17]
There are only very few Trojan horse programs mentioned by their name in the Internet. This may be a sign of their little number but it can also be a sign of the fact that the users have not noticed any problems with their software even if they are Trojans. As the source code of most of the cracking and hacking programs are available it is not very hard to write a Trojan. A normal program can be turned into a Trojan horse just by including the cracking program code into it. Nowadays when some of the software is more of a bloatware there is absolutely no way to predict if a program is a Trojan horse from the file sizes. If the Trojan horse program stays quiet and for example collects passwords there is very little risk of Trojan to get caught. Many of the known Trojans are malicious and have been noticed for this reason. The writers have ammpumced others after they have written them.
There are very few known Trojans only for NT but since the old DOS and Windows programs can be run under NT the number of possible Trojan horse attacks increase significantly. As an example of an NT trojan a member of l0pht society Yobie Benjamin wrote a Trojan horse program that was distributed by an attachment in e-mail. When the attachment was run it grabbed the password hashes from the computer and sent them back to the sender of the Trojan horse. The Trojan horse itself utilized Jeremy Allison's PWDUMP program. [7]
The Australian Computer Emergency Response Team (AUSCERT) received information from several independent sources that a software archive named PKZ300B.ZIP contains a Trojan horse program. After studying the situation they found out also that there is a selfextracting version of this archive file called PKZ300B.EXE. Both of these files were distributed in the Internet and on various dial-up BBS systems.
These files were claimed to be the 3.00B version of PKWARE Inc.'s shareware DOS data compression utility, PKZip. However the Trojan horse program did not do any compression nor did it extract files but it destroyed all the information on users hard drive. On 5th May 1996 when the original article was written the latest release of PKZip from PKWARE was v2.04G. Indeed PKWARE had not released a version 3.00 of PKZip at that time. [19]
On the NT server version 4.0 a new Registry entry
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Lsa
was introduced. The purpose of this key is to enable easier password synchronization
between NT and other operating systems. When the password of the users is set or
changed the clear text value of password, username and RID (relative domain id) are
forwarded to the DLL's that are listed under the Lsa-key value mentioned above. It would
be easy to write a program that adds the name of a malicious DLL under this registry
entry. The DLL could broadcast all the username password pairs into Internet or do
something else. This is why it is important to check that there is absolutely no extra
DLL's named in this registry entry. There are no known Trojans using this security issue,
but a one could be coded with little effort. [20]
Macro languages create a great opportunity for Trojan horse writers. For example Microsoft's Visual Basic for Applications (VBA) tries to standardize the macro language used across most of the Microsoft's products. VBA is capable of doing disk operations and could run for example any program on the hard drive or delete a file. Of course Visual Basic for Applications is not the only macro language suffering from the possibility of exploit. Practically all of the macro languages can be exploited in this way. A malicious cracker equipped with VBA coding skills and the knowledge that NT 4.0 has ROLLBACK.EXE program that removes the whole installation when it is run could do very bad things. For example he could write a Word document Trojan horse that rolls back the whole NT installation when the document is opened. An average administrator does not probably know about the risks related to ROLLBACK.EXE and thus will not remove the program. The most uncomfortable thing about this program is that it comes with the default installation of NT 4.0. [21]
Windows NT in itself is resistant to Master Boot Record (MBR) viruses. Once the NT operating system is up and running it prevents the programs from writing straight to disk by using BIOS or DOS services. MBR virus can come to an NT machine in two different ways. If an infected floppy is in the floppy drive when the power is turned on the virus will copy itself from the floppy to hard drive before NT is started. The other way for an NT machine to get infected is through another operating system that is installed in the computer. When the other operating system such as DOS or Windows is in use the infection may be transferred to the hard drive. In both cases none of the MBR viruses can reproduce after NT is booted up and the NT protected mode hard disk drivers are loaded. Even if the MBR viruses cannot reproduce in NT environment, some of them can cause serious harm such as NT not booting up or loss of data. The removal of MBR viruses is usually quite simple if you have clean boot disk and virus removal software.
Boot record viruses use the same two ways of infecting the file system as the MBR viruses. Boot record viruses may also destroy data or cause crashes during the boot-up. [22]
Most of the DOS file viruses function "correctly" under a Windows NT DOS box. Direct-Action-File-Viruses will typically do all the same things under NT's DOS box, as they would do under a real DOS. Memory resident viruses can hook into the DOS system services and stay resident for the whole lifetime of the NT DOS box. These memory resident viruses will however die once the NT DOS box is killed. Memory resident viruses cannot infect other NT DOS boxes through memory since each process has its' own protected memory space. But the memory resident virus can be transferred into other NT DOS boxes via disk access. Memory resident virus can infect an executable file on the hard disk and when the infected file is used in another NT DOS box the memory space of this other program will be infected.
All of the DOS viruses can do almost the same harm under Windows NT as they could do under DOS. How ever, the disk access is controlled by the operating system in NT environment. This makes it possible to restrict the harm done by virus with strict file permissions. Viruses can access only the same resources as the user who is logged in. Thus, the best way to restrict the damage is to install a virus scanner and use NT's own file permission functionality. File permissions should be tight enough also to prevent the users from accidentally tampering the important files.
Windows 3.1 viruses can also work under Windows NT. They usually hook up to such system services, which will notify them of all the new 16-bit applications starting in the same memory space. Thus, they can infect the other applications under NT much in the same way as they would infect them under Windows 3.1. If the new application is started in a separate 16-bit memory space the notification mechanism will not work and the infected application will be left unnotified. Also, the native 32-bit applications are resistant to Windows 3.1 viruses because their execution is not notified to the 16-bit memory space. [22]
Macro viruses can naturally spread between different operating systems. They can reproduce always when the application where the macro is started is compatible with the application where the macro virus was written. A Word macro virus written and sent from MacIntosh environment can try do all the same things in NT environment as it would do in Mac. Of course the file system permissions can be set in such a way that the harm will be minimized. Macro viruses are usually spread between companies through email attachments.
Any signs of native NT virus could not be found at the time of writing this paper. NT's 32-bit environment is much more complex and secure than the old DOS operating system. But knowing the amount of bugs in NT and the skills of crackers it is probably only a matter of time that we have native NT viruses. [22]
Certainly one of the best places to get up-to-date information about bugs and security holes are the hackers' and crackers' homepages and newsgroups in the Internet.
Some good starting points would be:
The list is in writer's order of preference. The best sites are on the top.
There are plenty of NT related web sites in the Internet. The following list is only small portion of the sites available.
This list is also formatted in author's order of preference. The best sites are on the top.
Microsoft has also reacted to the ever increasing amount of security exploits by setting up its' own Security Advisor pages. The information on these pages is pretty good. Of course the information has an obvious Microsoft bias. Reports on some of the newest solved security threats can be read here. Also the needed hotfixes and service packs can be downloaded from here. The pages can be viewed at <URL:http://www.microsoft.com/security/>
There are several books about NT Security. Among the best books according to book reviews and newsgroup articles are the following:
These books concentrate mostly on security issues. They go through security threats and countermeasures needed against them. In addition to all of this the books include pragmatic checklists for configuring NT 3.51 and NT 4.0 servers.
The tool list above is ordered so that the "bigger" and more developed tools are on the top of the list. "Smaller" and cheaper tools are at the bottom. An example of a pragmatic checklist can be viewed from <URL:http://www.ntresearch.com/ntchecks.htm>. Another check list is in the Microsoft Windows NT Server: Security Features and Future Direction White Paper written by Coopers & Lybrand L.L.P. Information Technology Security Services. This white paper can be downloaded from Microsoft's web site at <URL:http://www.eu.microsoft.com/ntserver/info/cooperswp.htm>
Microsoft has released some preliminary information about its forth-coming release NT version 5.0. The new security features include for example Kerberos V5 authentication, X.509 v3 authentication, SSL3, smart card support, crypto API and more exhaustive use of CIFS and SMB signing. [6]
Kerberos V5 authentication protocol is developed by Massachusets Institute of Technology (MIT) and it is a secure way to authenticate also in the Internet environment. There is plenty of material available about Kerberos at <URL:http://web.mit.edu/kerberos/www/>. [23] NT's Kerberos authentication protocol will support extensions for public key-based authentication in addition to password-based (secret key) authentication. Also the X.509 v3 Public Key Certificates will be supported for granting access to resources for subjects (for example users) that do not have Kerberos Credentials. This means that a non-NT user can be given access to resources such as password protected HTML pages etc. SSL3 will be used in Internet user authentication. [4]
Smart card support will be integrated in operating system. Smart card authentication combined with proper password policies will improve security substantially. Crypto API will be updated from version 1.0 to version 2.0. Crypto API 2.0 will provide both the old cryptographic functions from version 1.0 and the new certificate based functionalities. There is no analysis about Crypto API 2.0 available but the version 1.0 was criticized about its' weak cryptographic strength.[4]
CIFS file transfer protocol is designed to be used over Internet. It supports file transfers for anonymous users as well as for authenticated users. CIFS has many weaknesses that it inherits from the old LAN MANAGER environment. These security threats are explained in detail in Hobbit's paper named CIFS: Common Insecurities Fail Scrutiny. [15] This paper does not talk about Microsoft's new SMB signing authentication protocol, which is supposed to make the protocol stronger against attacks such as man-in-the-middle attack. In another newspaper interview Hobbit claims that SMB signing can be broken with trivial changes to L0pthcrack program. After this it is easy to play man-in-the-middle attacks. [24] Also according to NT Cryptographic Password Attacks & Defenses FAQ the SMB signing brings only moderate security. It uses MD4 hashes that require in worst case scenario 2200 years to be cracked with a Pentium Pro 200. With specialized hardware the attack will probably take only couple of hours.[12]
Still after all these changes that improve NT security substantially, doubts about NT's vulnerability in Internet environment have been made. As Windows NT 5.0 will be backward compatible it also has to provide the old LAN MANAGER protocols for old servers and clients to access its' resources. This means that the old and weak LANMAN hash based authentication has to be maintained. LANMAN support can quite probably be turned off from NT, but the real problem is education. Most of the NT administrators are not aware of the threats posed by the legacy LAN MANAGER authentication and will not turn it off for this reason. [25]
As the security issues are under constant change, permanent conclusions cannot be made. These conclusions are drawn from the presented material and might be subject to change even in a relatively short period of time.
Most of the NT Server security issues stem from the following issues: backward compatibility to old systems such as LAN MANAGER, the strict export restrictions on strong cryptographic products in United States, poor default configurations and bugs in implementation. The core of NT Server operating system can be considered secure. It is the services built around the core that have the poor design and flaws that compromise the security. As we saw, the cryptographic strength of old LANMAN hashes might have been enough in closed LAN environments where the amount of potential people trying to break in was very limited. In a modern Internet environment where all different kinds of operating systems must interact and where the people trying to get into your system can be from the other side of the globe, things like weak cryptographic algorithms are not acceptable. Some parts of the NT Server operating system are not on the level that Internet requires.
The suitability of NT Server for different environments in the light of these examples
The following suitability assessment is done in the light of previous examples and without any material to compare NT Server with the other operating systems. For these reasons nothing can be said about NT Server's security status compared to the other operating systems. However, some common sense conclusions can be made about its' suitability to different tasks in general.
The security level of NT Server is probably high enough for most of the closed LAN environments. This conclusion is based on the observations from everyday life that even the more basic security practices are many times not taken care of in these environments. Very little can be done with the operating system to enhance security if the server is located in a place where anybody can steal it or if the passwords are easy to guess. When this kind of basic work is done it is feasible for administrators to start to make also the operating system more secure.
When the company's network is connected to the Internet the potential of attacks explode. A firewall or a packet filter must always be used between the internal and external network. All the traffic between the networks should be disabled by default. When the company wants to release an Internet site for its' stakeholder the server should always be located outside the internal network. In the light of the presented examples it is fair to say that a well-motivated resourceful hacker or an advanced intelligence organization will be able to break in the system. The security of the NT Server, that is exposed to Internet, can be reduced by installing a firewall or a packet filter between the server and the Internet. In this way some of the traffic such as SMB protocol can be blocked out and the intruders work can be made considerably harder. If all the latest service packs are installed, and the server and the firewall are planned to support the security policy, the server may be safe enough for storing some semi-confidential information also. NT Servers that store substantial amounts of very valuable information such as micro payments should not be connected straight to Internet.
With the internal networks that are connected to the Internet through arrangements as described above we have to separate two very different security scenarios. In the first scenario the server has TCP/IP protocol disabled and in the second scenario the protocol is enabled. If the TCP/IP protocol is not enabled, the security threat is coming straight from the inside or from the outside so that the internal computers that have TCP/IP enabled are used as a gateway to attack the server. In all cases the number of clients that can act as a gateway for the attack must be minimized or totally eliminated. This can be done usually by disabling server services in client operating systems such as Windows 95 for example. After this the administrators have to go through who can access the computer connected to internal network and how good are the security practices. Technically the server's operating system will not survive professional attacks from inside even if the all the technical steps are taken to enhance the security. If configured right NT Server will quite probably be able to resist all the amateur attacks.
If the internal NT Server has TCP/IP enabled and all the other security practices support its' security, the server is probably safe enough for most of the business documents. Things like unencrypted email might be a more severe threat in many cases. As there are some holes in firewall enabling the outside traffic the security level is a bit lower than in the case where the TCP/IP protocol was disabled.
When there is a need for very high security in any of the scenarios above the only way to get it is with the use of strong cryptographic encryption. All the important information must be encrypted with strong algorithms and the keys must be carefully looked after. With this kinds of arrangement the security risk of intruders getting any useful information is usually lowered to a level that is acceptable.
Things that administrators should do
The first and most important thing for administrators to know is that security risks exist. Administrators should known at least so much that they won't even think about connecting their server containing operational data straight to Internet without firewalls and without any configuration after installation. Administrators should know that Internet can be a very insecure place and if they don't know how they should connect to it, they should find an expert that knows. To gain this minimum level of knowledge all the administrators should read at least few of the security documents in Internet or one of the books mentioned in this paper.
As practical everyday advises the following could be given. Administrators should use the administrative account only when it is absolutely necessary. They should have another account that they are using while they are not administering the system. Also the administrators should never access the Internet while logged on as an administrator.
When a new version of NT Server operating system comes to market it is of course a good idea to wait and see how the new version works. However, some time after the new version release a part of the security fixes is only made for the latest version. For this practical reason servers should always have an operating system version that is enough new. To be prepared against the bugs all the service packs should be installed once they are considered stabile. And if the administrators have time also the hot fixes concerning security should be installed.
When more security is needed closer look at the NT Server should be taken. Many of the good security features such as auditing, account lockout after unsuccessful logon attempts and the password validity check that comes with the operating system version 4.0 should be used before running after third party products.
Administrators should talk more about the security issues and demand better service from Microsoft. So far the cost of not making the operating system more secure has been so low that Microsoft have not paid very much attention to it.
Things that Microsoft could improve
As the NT Server meets the Internet more and more often Microsoft should add more information about computer security in its' product. Because the NT Server is easy to use some administrators might think that the security issues are also taken care of. Microsoft has in this respect the responsibility to make the operating system more secure and inform the customer about the new stricter security requirements that the Internet brings with it.
Microsoft should include material about the computer security in general and about the security of NT Server. Especially the NT Server specific parts should be supplemented with online material through Internet to keep the administrator up-to-date. Material should emphasize the on-going process nature of the security administration.
The default installation of NT Server is too insecure at the moment - especially for the Internet use. If one very strict default installation is not enough to satisfy the different customer needs other kinds of installations should be offered also. For example there could be a separate LAN installation and an Internet installation. The Internet installation would have very strict configurations and all the unnecessary components should be left out. Also a security Wizard could be introduced to make some of the advanced security setting changes easier.
Microsoft should wake up from the rosy dreams and start to do even more about solving the severe design flaws and implementation bugs. More money should be allocated for fixing the problems and less could be given to such unproductive tasks as marketing department poking at other operating systems and their flaws.
There will always be bugs in such a big system as the NT Server operating system is already today. The operating system is ready for closed environments and low risk environments. However, it is not ready for Internet so that one could trust the main business only in the hands of NT Servers in this environment. It would be interesting to see how NT Server compares with the other operating systems. At the moment there is still much to be done in the operating system. Hopefully Microsoft will do the changes early enough for the sake of its' customers and for the sake of its' own business. With such a healthy operating system core it is hopefully not too late to react.
| ACL | Access Control List is used for discribing access permissions to computer resources suc as file system files and directories, registry etc. |
| API | Application Programming Interface is an interface of an program component that can be utilized by other programs etc. |
| DES | DES is a secret key cryptographic algorithm developed in the 1970s. It was made a standard by the US government, and has also been adopted by several other governments worldwide. |
| HTML | Hypertext Markup Language is used for writing web pages. |
| LAN | Local Area Network is a computer network that is used in a geographically small area. Today, the most used LAN technologies are Ethernet and Token Ring -technologies. |
| LAN MANAGER | LAN MANAGER is an old network operating system for sharing/accessing network resources. Microsoft was one of the software houses developing this network operating system. |
| MBR | Master Boot Record is read by the computer usually from the hard disk in the beginning of the boot up process. It gives "further" instructions for boot up sequence. |
| MD4 hash | MD4 hash is a cryptographic hash function developed by RSA Data Security. |
| NetBios | Network Basic Input/Output System is an API for network resources. |
| RFC | Request For Comments are Internet specifications that become "standard" if there are enough many inividual implementations of it. |
| SMB | Server Message Block is protocol that NT uses for connecting to/sharing network resources. |
[1] SAFEsuite: adaptive Security Management Solutions. <URL:http://iss.net/prod/brochure.html>
[2] ISS. Comprehensive Enterprise Network Security Assessment. <URL:http://www.iss.net/prod/cnsa/cnsa.html>
[3] Malmgren Robert. NT Security - Frequently Asked Questions version 0.39. <URL:http://www.it.kth.se/~rom/ntsec.html>
[4] Coopers & Lybrand L.L.P. Information Technology Security Services. White paper on Microsoft Windows NT Server: Security Features and future directions. <URL:http://www.eu.microsoft.com/ntserver/info/cooperswp.htm>
[5] Amoroso Edward G. Fundamentals of Computer Security Technology. Prentice Hall, 1994.
[6] WinNuke Testing Ground. <URL:http://206.148.240.160/~dirk/winnuke.html>
[7] Lange Larry. The Rise of the Underground Engineer. <URL:http://techweb.cmp.com/eet/whitepaper/paper1/paper1a.html>
[8] Rutstein Charles B. Windows NT Security: A Practical Guide to Securing Windows Nt Servers and Workstations. McGraw-Hill Ncsa Guides, April 1997
[9] Sutton Stephen A. Windows Nt Security Guide. Addison-Wesley Pub Co, December 1996
[10] Windows NT Security Issues: Practical recommendations for securing File System and Registry. <URL:http://ntsecurity.com/A2NT/default.htm>
[11] Windows NT Security Issues. <URL:http://www.somarsoft.com/security.htm>
[12] Ramsbottom Alan. FAQ: NT Cryptographic Password Attacks & Defences. <URL:http://ntbugtraq.rc.on.ca/samfaq.htm>
[13] GetAdmin.<URL:http://www.ntsecurity.net/security/getadmin.htm>
[14] Cryptographic Algorithms. <URL:http://www.cs.hut.fi/crypto/algorithms.html>
[15] "Hobbit". CIFS: Common Insecurities Fail Scrutiny. <URL:http://199.103.168.8:2433/avian/papers/cifs.txt>
[16] Ping o' Death Page. <URL:http://www.sophist.demon.co.uk/ping/>
[17] The RedButton. <URL:http://www.ntsecurity.com/RedButton/default.htm>
[18] RedButton Frequently Asked Questions. <URL:http://www.ntsecurity.com/RedButton/faq.htm>
[19] Phony PKZip Archive: Trojan Horse Alert. <URL:http://www.xanadu2.net/rrogers/trojan.html>
[20] Allison Jeremy. NT Password Trojan. <URL:http://www.ntshop.net/security/passworddll.htm>
[21] Data and WAN Issues. <URL:http://www.info-com.com/swlcmg/news/dataoct.htm>
[22] Understanding Virus Behavior in the Windows NT Environment. <URL:http://www.symantec.com/avcenter/reference/vbnt.html>
[23] Kerberos: The Network Authentication Protocol. <URL:http://web.mit.edu/kerberos/www/>
[24] Swoyer Stephen. Backward Compatibility Keeps NT 5.0 Vulnerable. <URL:http://www.entmag.com/archive/1997/sept10/091021.html-ssi>